Despite the guarantee of free access to information enshrined in the Universal Declaration of Human rights, the number of countries engaging in some kind of internet censorship continues to grow rapidly around the world. The issue of internet censorship is now central in policy, communication, and technology debates. It has also become of interest to scholars in the humanities and social sciences who think seriously about the relationship between culture, politics, and the internet.
But in order to build a rich conversation about the causes and consequences of internet censorship, we must first understand how internet censorship works, especially on a technical level. This two-part post lays out a (simplified) explanation of internet censorship technologies. The first of these gives a broad overview of how the internet works, while the next post builds on these foundations to explain how various censorship techniques can block information on the internet.
How the Internet Works
To understand how internet censorship works, as well as how to circumvent such obstacles, we must first get a grip on how the internet works. Consider this over-simplified model of just what happens when you view a webpage.
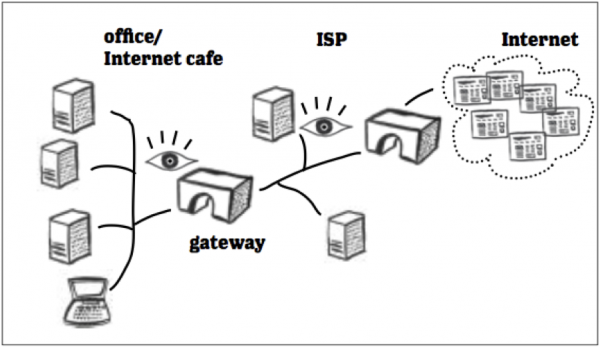
When you log onto the internet at your home, office, school, library or internet café, you are connecting through an Internet Service Provider (ISP), such as Comcast or AT&T. The ISP then assigns your individual computer an IP Address, which is similar to a postal address in that it is used to identify you and transport information. Anyone who learns your IP address can find out what city you’re in, and other institutions such as your ISP, internet café, library or business can find out more, such as which building you are in and even which computer you are using. Government agencies, to the extent that they have access to said institutions, may know these details as well.
Your Internet Connection
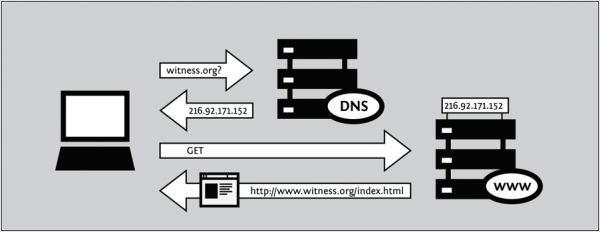
Like computers, web sites have IP addresses as well. When you browse to a certain web page on your computer, you are actually requesting information from a particular IP address. For instance, the IP address of the THL site is 174.129.208.156. (Try entering that into your browser window – it goes to THL!) But because these IP addresses are cumbersome and difficult to remember, the Domain Name System (DNS) allows IP address to be associated with human-readable “domain names” such as townsendlab.berkeley.edu.
DNS
So, when you type in http://townsendcenter.berkeley.edu into your web browser, a series of things happen:
- Your computer sends the domain name "townsendlab.berkeley.edu" to a selected DNS server, which returns a message containing the IP address for the server that hosts the Townsend Humanities Lab (currently, 174.129.208.156).
- The browser then sends a request to your ISP for a connection to that IP address.
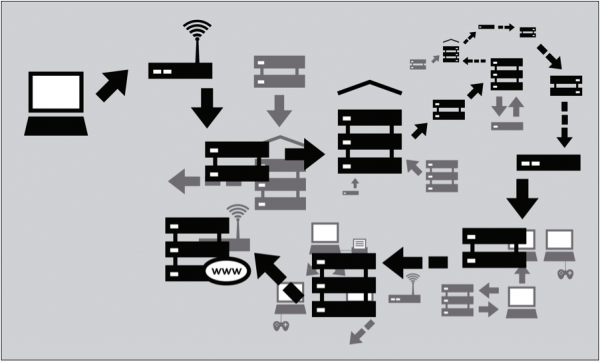
- The request goes through a series of routers, each one forwarding a copy of the request to a router closer to the destination, until it reaches a router that finds the specific computer needed.
- The message from the Web site to you travels through other devices (computers or routers). Each such device along a path can be referred to as a "hop"; the number of hops is the number of computers or routers your message comes in contact with along its way and is often between 5 and 30.
- This computer sends information back to you, allowing your browser to send the full URL and receive the data to display the page. Et Voila!
"Hops"
In order to send packets of information around from server to server, ISPs must rely on set internet protocols as well as on national and international infrastructure that supports such connections. This set of structure and conventions are commonly referred to as the “backbone” of the internet.
Protocols allow data and resources to be shared in a coherent way. For instance, the internet uses the concept of numbered ports to manage connections into different kinds of requests. For instance, normal web-browsing uses port 80. But the Web is only one facet of the internet. File transfer, for instance, uses 20/21 and email uses 25, 53, or 143. Try entering “townsendlab.berkeley.edu:80” into your browser. It works because that’s the default port for web browsing. Now try “townsendlab.berkeley.edu:20”. Hint: it probably won’t work.
The backbone is also made up of major network equipment installations which are connected to one another via fiber-optic cables and satellites. These connections enable communications between Internet users in different countries and continents. National and international providers connect to this backbone through routers sometimes known as gateways, which are connections that allow disparate networks to communicate with each other. These gateways, just like other routers, may be a point at which Internet traffic is monitored or controlled.
Why This Matters
For the average internet user, these complex processes remain blissfully unseen. We don’t have to understand the tech lingo or internet jargon to find out what movie’s playing tonight at the Shattuck Cinema. But in order to understand how information is censored or filtered on the internet, a discussion of these processes become absolutely necessary because the mechanism that blocks information can act on any step of the internet system.
Consider DNS servers. Originally, this system was created in order to translate between human-readable domain names and IP addresses. However, these servers can also be used as censoring mechanisms by checking requested domain names against an existing “blacklist” and preventing the proper IP address from being returned. This is one way to effectively block access to the requested information from that domain.
Censorship can thus occur at different points in the Internet system, from whole networks, certain ports, individual domains or even specific keywords identified by filtering software. The only way to adequately bypass censorship or create effective policy is to identify the specific censorship techniques that are used.
So how exactly do governments, corporations, and other information-wary actors work to limit information traveling across the information super highway? Visit my IP address next week for more.