Internet Censorship (Part 2): The Technology of Information Control
Last week, I provided a simple diagram of how the internet works. I did this because knowing how information flows through this complex process can help us understand how information is blocked, filtered, or censored. Here, in the second part of my blog post on internet censorship, the mechanisms of internet control is explained in more detail.
Internet censorship, like all censorship, can take multiple forms, from filtering and blocking content to monitoring and penalizing users who access certain content. Governments may both define what to block and implement the technological process of blocking, or they may create legislation, extra-legal incentives, or policy to compel “autonomous” technological firms to carry out the blocking and surveillance for them. Often the most simple strategy is to demand the removal of websites with illegal content.
Even within the technical domain, Internet censorship refers to a plethora of tools and strategies to prevent information from reaching users. So it is important to remember that when we refer to “internet censorship” we are not referring to one thing, one software, one point of blockage. Censorship can occur at one point on the internet circuit, can manifest as a blanket filter for all connections in a given country or can be micro-focused on individual sites, machines, and even words.
The following is a list of the most common internet censorship technologies:
DNS Tampering
In countries where authorities have control over domain name servers, officials can “deregister” a domain that is hosting nefarious content. As explained last week, this makes the website invisible to the browsers of users seeking to access the site because it prevents the translation of domain names to site IP addresses. This is similar to receiving the wrong phone number of the person you wish to call.
IP Blocking
Governments with control over internet service providers can blacklist certain IP addresses of websites they do not like. When you request access to a site, your request is monitored by surveillance computers, which check your request against a list of blacklisted IP addresses. If you are trying to reach one of these forbidden sites, the internet service provider will drop the connection, causing it to fail. For instance, in China, where international-gateway servers control the flow of internet information in and out of the entire country, requests to banned sites are intercepted by these mega-servers, which then interrupt the transmission by sending a “reset” request to both your machine and the one you wish to reach. This causes the connection to hang up, preventing access to the information you want. If the target Web site is hosted on a shared hosting server, all sites existing on the same server will be blocked as well, even if they are not targeted for filtering themselves.
Keyword filtering
IP address filtering only blocks websites that are explicitly blacklisted (or those that share the same server). But if you’re a government wanting to block all information on subject X, this can be a problem. Not only are there billions of websites, but new ones are created all the time, making it nearly impossible to create a fully updated list of sites of forbidden content.
For a more powerful censoring technique, governments may use URL filtering. This mechanism scans the requested Uniform Resource Locator (URL) string (e.g. www.website.com/how-to-overthrow-Iranian-regime/) for target words. If the URL includes forbidden terms, the connection will be reset.
Packet filtering
An even more fine-grained strategy is also one of the newest and most sophisticated internet censoring technologies: packet filtering, or scanning the actual contents of each page. When data is sent over the internet, it is grouped in small units called packets. Think of a packet as a letter in an envelope: it contains both the contents of your letter as well as instructions of where the letter is suppose to go (i.e. sender and receiver addresses.) Packets are relayed from computer to computer using routers, which are like the Internet’s postal service.
IP address filtering can only block communication on the basis of where packets are going to or coming from – that is, their address – not the actual material of their contents. The process of deep packet inspection examines packet contents for banned keywords. Communication identified as containing forbidden content can be disrupted by dropping the connection. Users may receive one of a number of error message on their browsers, none indicating explicitly that they are being censored.
Less Common Strategies
These strategies—DNS tampering, IP blocking, and keyword filtering—are the most common methods used to implement wide-ranging internet censorship. But other techniques may be used. For instance, traffic shaping can be used by governments or corporations to delay access to some sites, giving the misleading impression that sites are slow or unreliable. This technique is sometimes used by ISPs to discourage peer-to-peer file-sharing networks such as BitTorrent.
Individual port numbers can also be blacklisted, restricting access to services such as Web or email. This is often done by corporations who wish to restrict certain behaviors by their employers while on work machines—instant messaging, for example.
Some countries even require individual personal computers to include software that filters internet content. In China, for instance, all PCs must be sold with software that would allow the government to regularly update computers with an ever-changing list of banned sites. This technique is commonly used in the United States as well to set up filtration systems in libraries, schools, and public internet cafes.
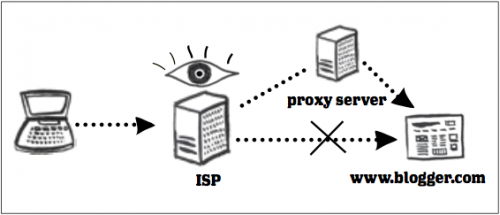
Because blocking is often disguised as a technical error or connection problem, it is difficult to determine whether you are experiencing internet censorship, which technique is being used, or who is doing the blocking. This also makes it difficult to circumvent censorship. While some devices such as proxy servers or virtual private networks (VPN) are widely used to get around filters, they may not work in all cases.
Owning the Internet
Now that we know how internet censorship is actually done, we are much better equipped to engage in a rich and nuanced discussion about accountability. For instance, most of us already knew that governments are involved in wide-spread internet censorship. But it is also important to understand the role of internet service providers, software corporations, and internet companies.
For instance, take ISPs. Sometimes a government directly owns or manages the ISPs. In other cases, Internet service providers and hosting companies are privately owned but often abide by government censoring demands in order to continue doing business in a particular country. The number, autonomy, and distribution of ISP in a particular country can have a profound influence on the effectiveness of internet censorship.
Or take software-makers. Governments often rely on private corporations to provide the technology and expertise to implement censorship. Oftentimes these corporations are multinational. The danger is most pronounced when these corporations work in partnership with undemocratic regimes in order to set up nationwide censorship regimes.
Seemingly "anti-censorship" internet companies such as Google are guilty, at times, of cooperating (and thus accused of condoning) with such effects by filtering their search results in particular countries and handing over their data on users’ search records.
Even "off-line" construction and infrastructure firms have a role to play. As we have seen, some governments design their national telecommunicaitons systems to have single “choke points” whereby they can control their whole country’s access to certain sites or services.
Addressing internet censorship will require a sustained conversation between software engineers, web developers, policy makers, area experts and humanists. This post was designed to get humanists up to speed on the technology of the problem. Now its time for humanists to teach engineers and policy analysts what censorship does to our communication, our creativity, and our humanity.
More Resources
How to Bypass Internet Censorship
Understanding Censorship Circumvention